Hiding in the Shadows: How Threats Exploit the Unprepared
Every 39 seconds, a cyberattack strikes – and most victims don’t see it coming. In today’s hyperconnected world, attackers no longer need to break in. They wait patiently in the dark corners of your network—undetected, automated, and already inside.
NeoSystems’ recent webinar, “Hiding in the Shadows,” exposes this chilling reality and what it takes to shine a light on modern threats before they take hold. With sophisticated nation state cyberattacks increasingly targeting our DIB, organizations must adopt robust measures to thwart threats and ensure their data and infrastructure remain secure. At the heart of this issue is visibility and preparedness, best practices that many businesses overlook until it’s too late.
In this blog, we break down urgent insights from NeoSystems recent webinar, “Hiding in the Shadows,” exposing how today’s adversaries operate, why unseen vulnerabilities are their totem of success, and what actions organizations must take now to stay ahead of the breach.
Understanding Modern Threats
Let’s pull back the curtain on the cyber battlefield.
Cyber threats have evolved far beyond the lone hacker in a hoodie typing away in a dark basement; Today’s threats consist of highly-coordinated and stealthy adversaries running targeted campaigns—often orchestrated by state-backed actors from nations like China, Russia, North Korea, and Iran—targeting national infrastructure and private industry alike. Which is why visibility into your network is no longer optional.
Major defense contractors are experiencing nearly 20 million cyberattack attempts every single day, most of which are focused, persistent, highly automated, state sponsored and increasingly powered by AI.
automated, state sponsored and increasingly powered by AI.
The lesson is clear. “You can’t protect what you can’t see.” – CISA
Cybercriminals don’t rush – they lurk undetected, spending an average of 208 days within a network before discovery, extracting valuable information or establishing long-term footholds.
Notably, 82% of breach notifications come from external parties, such as law enforcement or the perpetrators themselves, leaving businesses blind to their internal vulnerabilities.
Organizations that leverage SOC As-a-Service with AI analytics like live threat maps take advantage of real time detection, giving teams a clear view of what’s happening—before it’s too late.
“The attacker only has to get it right once. We have to get it right every time.”
Proactive Measures for Defense
To keep pace with today’s attackers, businesses must stop reacting and start anticipating. That begins with a shift in mindset: Assume breach. Operate as if adversaries are already inside and build your defenses accordingly.
Here’s what that looks like in practice:
Practical Proactive Steps
-
Real-Time Threat Detection
Implement solutions that monitor system activity continuously and flag anomalies instantly. AI-driven detections help spot unusual patterns humans might miss.
-
Strong Identity and Access Management (IAM)
Enforce strict user access controls. Use multi-factor authentication (MFA) and lock down credentials to block easy entry points.
-
Baseline your Assets and Maintain
Know what “normal” looks like across your network and establish a baseline, so deviations trigger immediate investigation.
-
Continuous Monitoring and Patching
Regularly update and patch software vulnerabilities before they become open invitations to adversaries.
-
Tabletop Exercises
Test your response plan before it’s needed. Simulate cyber incidents to test your organization’s response capabilities. Practice makes perfect and helps uncover gaps in your plan.
-
Adopt a Zero Trust Mindset

Adopt a never trust, always verify principal, by default. Zero Trust isn’t a product—it’s a security model that assumes breaches are inevitable or have already occurred. Implement a strategy to minimize risk, reduce attack surfaces, and block unauthorized access at every turn.
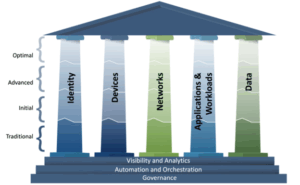
As illustrated in the CISA Zero Trust Maturity Model, the five pillars—Identity, Devices, Networks, Applications, and Data—form the foundation of a security strategy that assumes breach.
Case Studies in Cyber Resilience
Real-world events from the webinar highlight how visibility and speed can stop threats cold.
Case 1: Stopping SolarWinds
During the SolarWinds breach, Sierra Nevada Company (SNC) leveraged Zero Trust principles alongside continuous monitoring to detect an unauthorized outbound connection in real time. Immediate action blocked the intrusion before it escalated—avoiding serious damage.
Case 2: 9 Million Attacks in 30 minutes
A misconfigured firewall opened the door—briefly. In just 30 minutes, over 9 million brute-force attempts hit SNC’s network. Their detection tools flagged the spike instantly, allowing the team to close the gap and prevent a breach.
These moments prove a simple truth:
“You can’t respond fast if you can’t see what’s happening.”
The Role of AI in Cybersecurity
Adversaries are already using AI to gain the upper hand—automating phishing campaigns, scanning for vulnerabilities, and adapting to defenses in real time. To keep pace, defenders must do the same.
Here’s how AI strengthens cyber defense:
Real-Time Data Analysis
AI can scan tremendous amounts of data in seconds to detect anything out of the ordinary. The same action taken by humans would take days or even weeks to complete.
How AI Strengthens Defense Strategies:
- Analyzing Large Volumes of Data: AI can process terabytes of log data in real time, spotting subtle abnormalities that humans might miss.
- Pattern Recognition: Over time, AI can learn “normal” system behavior and identify deviations more accurately.
- Automated Responses: Advanced AI systems can autonomously take corrective actions, such as isolating compromised systems or blocking unauthorized access attempts in real time.
Organizations like SNC Defensible Security are already using AI to combat evolving threats. For example, during the early days of the COVID-19 pandemic, AI detected a sudden drop in cyberattack attempts from China, enabling the team to adjust defenses for impending operational shifts.
Key Takeaways for Cyber-Resilience
Today’s threats move fast. Your response needs to move faster. These are the core pillars of an effective defense strategy.
- Speed wins: Threat actors move with lightning speed; vulnerabilities are identified and exploited almost immediately. Keeping defenses agile and dynamic is crucial.
- Visibility is Non-Negotiable: Ensure comprehensive, real-time monitoring that integrates tools and teams for effective threat detection and resolution.
- Leverage AI and Automation: Threat actors already weaponize AI. You need automation and analytics that keep pace—and outmaneuver them.
- Assume You’re Breached: Always operate under the assumption that attackers are already inside. Proactively hunt for signs, test your defenses, and close the gaps – daily.
Don’t Get Caught Off Guard
Cyber threats aren’t slowing down—and neither should your defenses. With the right tools, visibility, and proactive mindset, even small and mid-sized businesses can stay ahead of nation-state attackers and advanced persistent threats.
Watch the full webinar: Watch Now.
Learn how to spot what others miss, adopt a zero-trust strategy, and use AI to outpace modern cyber threats. Equip your team with the knowledge and tactics to move from reactive to resilient.