Getting the Scope Right: The Foundation of CMMC Level 2 Certification
In this blog, we’ll explore the essentials for successful CMMC level 2 scoping, including:
- Key considerations and steps to accurately prepare your Level 2 assessment scope
- A breakdown of Level 2 Asset categories and requirements
- The pivotal role of the external service provider (ESP) and impact to your compliance scope
Why are we talking about scoping? For defense contractors, subcontractors, or suppliers, the surest path to CMMC Level 2 certification success depends heavily on an accurately defined CUI boundary, or “CMMC assessment scope”.
The wait may be over, as the DoD has finalized its expectations of the CMMC program, but the lion’s share of defense contractors are just getting started, many with a heavier lift than others. This blog provides defense contractors with best practices in getting started on the right path with scoping for CMMC Level 2 certification.
So, what is scoping?
In the terms of CMMC, scoping is the process of defining your assessment boundary. By considering all the applicable systems, applications and processes that store, transmit and/or process Controlled Unclassified Information (CUI), and the people, process and technologies that provide security or capabilities to your CUI boundary, you establish your CMMC assessment scope.

Getting the Scope Right. Think of your CMMC assessment scope in the context of laying a foundation of a house. If done correctly, it provides the stability and structure needed to build upwards with confidence. Your assessment scope serves as a blueprint for your assessment and becomes the building blocks that will support everything else in the process. On the contrary, missing key elements or presenting an assessment scope that is incongruent with your documentation is like a poorly constructed house. One flaw at the foundational level can ripple upwards, compromising everything that follows. Precision in scoping for CMMC is non-negotiable. For CMMC, a well-defined CUI boundary or ”assessment scope” is the bedrock of certification success.
Begin with the End in Mind. Imagine it’s assessment day. Your system security plan, asset inventory list, network diagram, and policies and procedures are organized flawlessly. Every asset is accounted for, every artifact in its place. Everything in scope is sufficiently safeguarded, and your documentation succinctly illustrated. Your assessor begins down their list of questions, but you’re ready and feeling confident that you have the answers. This is the CMMC conformance dream—and getting there begins with having a good partner by your side, a well-defined assessment scope, and a roadmap to CMMC Level 2 Certification Success.
What is required for CMMC Level 2 Certification? To get started, organizations seeking Level 2 certification (OSCs) need to identify all systems that handle federal contract information and/or Controlled Unclassified Information. Specifically, contractors are required to:
- Document all assets in an asset inventory list that store, process, create, or transmit CUI.
- Provide a network diagram of the assessment scope, accurately categorizing all in scope assets.
- Populate a systems security plan (SSP) detailing how all in-scope assets and systems are being protected utilizing NIST 800-171controls and objectives.
4 Steps to CMMC Level 2 Certification Success
When it comes to getting started on your journey to CMMC, every step counts. Here are 4 steps to set yourself up for assessment success.
Step 1. Choose your Services Provider Wisely. While most service providers are qualified and capable of delivering the services they offer, there are some that are not. Be wary of claims that sound too good to be true; they probably are. Look for an ESP or MSP that holds or is pursuing their CMMC Level 2 certification; employs Certified CMMC Assessors or Certified CMMC Professionals; has hands on experience leading clients through a CMMC level 2 assessment; and has been implementing NIST 800-171 controls and/or has successfully led or participated in a Joint Surveillance Voluntary Assessment (JSVA).
Why this is important. A service provider’s JSVA experience represents a significant investment in understanding and validating compliance requirements. This experience directly translates into more effective, efficient, and successful compliance programs for their clients, ultimately reducing risk and accelerating the path to CMMC certification.
Step 2. Define Your Sensitive Data. Based on your contract(s), identify where Federal Contract Information (FCI) and Controlled Unclassified Information (CUI) is created, stored, processed and transmitted throughout your environment.
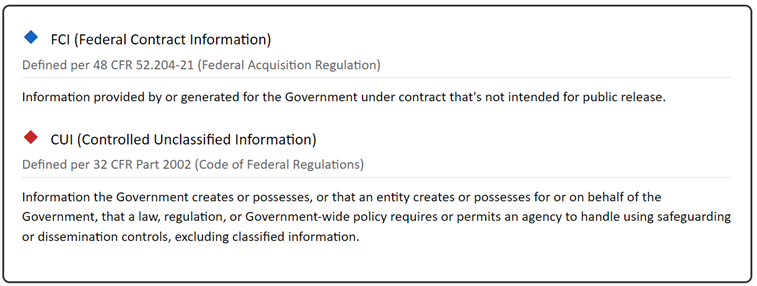
Think of federal contract information (FCI) and Controlled Unclassified Information (CUI) like a set of nested boxes. Let me explain:
Federal Contract Information (FCI) is like a large box. It contains any information you get from or create for the government while doing contract work. The only things that don’t go in this box are public information (like your website) and basic business transactions (like sending an invoice).
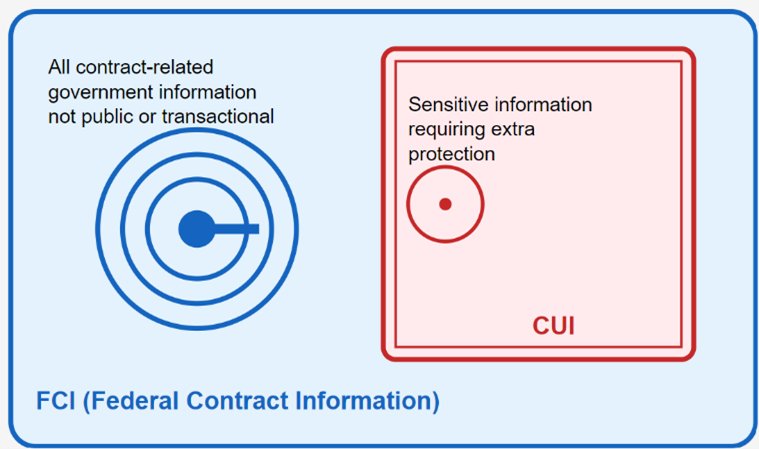
Controlled Unclassified Information (CUI) is like a special, smaller box inside the FCI box. This box holds more sensitive government information that needs extra protection. Think of things like technical drawings, research data, or private personnel information. While not classified, this information could cause problems if the wrong people got it.
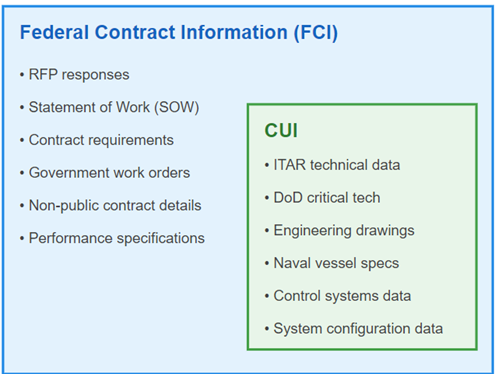
Examples of FCI vs. CUI
Step 3. Define the Scope, or “Assessment Boundary”.
Identify the people, processes, technologies and facilities that have access to FCI/CUI in your systems and define your boundary. In this step, consider the third-party service providers, or external service providers, suppliers and customers that send and/or receive CUI to and from your defined scope.
- People: Who in the organization has access to CUI?
- Processes: What physical and digital processes, from sales to shipping, involve CUI?
- Technologies: What hardware, software, Enterprise Resource Management (ERP) applications, systems and tools store, process or transmit FCI and CUI?
- Facilities: Where physically, within your facilities as well as in shared resources like datacenters or network operation centers (NOCs), is FCI and CUI stored, processed, or transmitted?
- External service providers: What third-party entities deliver a service that affects the confidentiality, integrity or availability of your CUI boundary and scope? What Cloud Service Providers (CSPs), Managed Service Providers (MSPs) and/or Managed Security Service providers (MSSPs) store, process, or transmit CUI or are involved in processes, procedures, or tools that protect CUI.
Step 4. Document the environment. Once you have identified all the “assets,” you can begin populating your documentation, with the following elements required.
- Create an asset inventory list. Using the asset categories referenced in the 32 CFR part 170 and CMMC Level 2 scoping guide, label each asset and workflow that accesses CUI. Consider this list the living inventory of everything that keeps your business running.
- Create a CUI Data Flow Diagram. Map how the FCI and CUI flows from the DoD to your environment and any of your subcontractors and suppliers.
- Create a Network Diagram illustrating all the assets in the asset inventory including those where FCI/CUI is being stored, transmitted or processed, using the categories provided by the DOD CIO’s Level 2 scoping guide. DoD’s CMMC Level 2 Scoping Guide
- Develop and maintain risk-based policies and procedures procedures that address how your CMMC assessment scope is protected and meets all NIST 800-171 security requirements.
Categorizing your CMMC Assets for Success
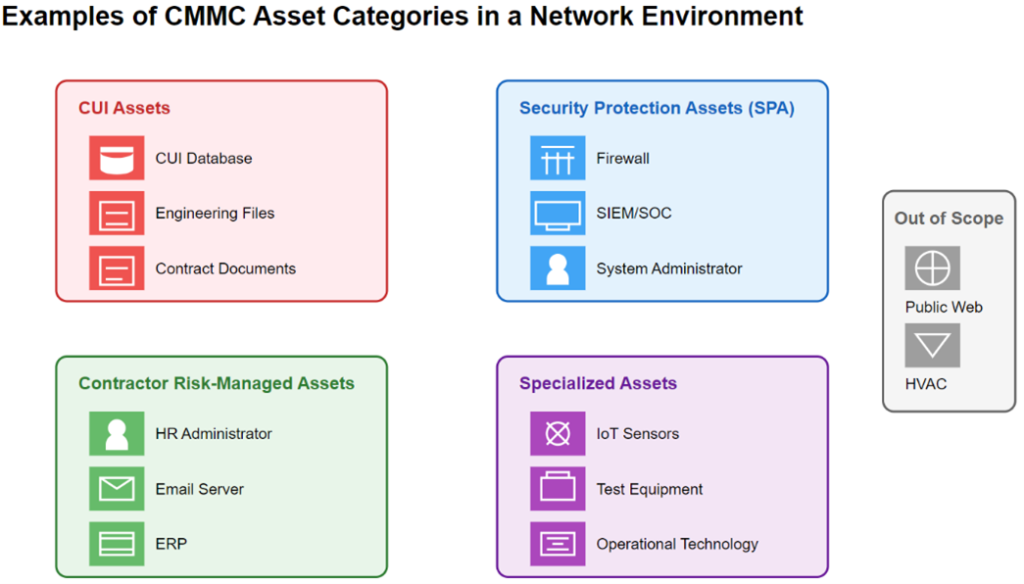
Now that you have defined the people, processes, technology and facilities that need protection in your CMMC assessment scope, you can begin categorizing these assets. Your assessment scope will encompass a range of asset categories, each with specific definitions, requirements and handling requirements.
- Controlled Unclassified Information (or CUI) Assets
- These are assets that directly handle CUI, and can include people, processes, technology, and facilities.
- Contractor requirement: Must be documented in the asset inventory, SSP, and network diagram, and will be assessed against all Level 2 security requirements.
- Security Protection Assets (SPA)
- These are assets that provide security functions or capabilities to your CMMC assessment scope. SPAs may include people such as your system administrator, technology such as your firewall, vulnerability tools, surveillance cameras, multi-factor authentication, antivirus software, IDS/IPS, and security management tools used for monitoring and logging activity (e.g. SOC/SIEM).
- Contractor requirement: Document in asset inventory, SSP and network diagram. Be prepared to be assessed against Level 2 security requirements that are relevant to the capabilities being provided.
- Contractor Risk-Managed Assets (CRMAs)
- CRMAs are assets that may handle CUI but have policies and procedures in place to prevent unintentional CUI interaction.
- Contractor requirement: Document these assets in the asset inventory, SSP, and network diagram, and show how you are safeguarding from CUI assets through your practices and risk-based policies and procedures. CRMAs are not required to be physically or logically separated from your assessment scope.
- Specialized Assets
- These assets, such as IoT devices, operational technology (OT), Government furnished equipment (GFE), Restricted information systems, and Test Equipment, can store or transmit CUI but are protected using the contractors’ risk-based security policies and procedures.
- Contractor requirement: Document in the asset inventory, SSP, and network diagram, and manage using risk-based security policies. Be prepared to show how these assets are utilizing the risk-based policies, procedures and practices.
- Out-of-Scope Assets
- These assets cannot process, store or transmit CUI, nor do they provide security for CUI assets, remaining physically or logically separate from your assessment scope.
- Contractor requirement: While these assets are not in the assessment scope, be prepared to justify their exclusion from your CMMC assessment scope.
So, what exactly is an External Service Provider, or ESP?
As defined by the Final Rule, an External Service Provider is a third-party organization such as a consultant, managed IT service provider, or a facility that a defense contractor utilizes for the provision and management of their IT and/or cybersecurity services on behalf of the organization.
The types of services provided by an ESP can range from monitoring endpoints and running scans of the environment to providing incident response services and handling security related data (e.g. configuration or log data) on their own assets and software.

And while CSPs, MSPs and MSSPs are popular flavors of ESPs, in the eyes of the DoD, not all ESPs are treated the same.
Let’s consider the Cloud Service Provider (CSP). In general terms, A Cloud Service Provider offers a Software as a Service (SaaS), Platform as a service (PaaS), and infrastructure as a service (IaaS), over the internet without the need for local infrastructure.
However, if a cloud service provider stores, processes or transmits CUI on nonfederal systems, they are required to meet FedRAMP Moderate compliance requirements. FedRAMP (Federal Risk and Authorization Management Program) is a U.S. government-wide program designed to standardize the security assessment, authorization, and continuous monitoring of cloud services used by federal agencies. It ensures that cloud services meet strict security requirements, providing a consistent framework for assessing and managing risks.
For Federal agencies and organizations handling CUI, trusting a cloud service with a formal FedRAMP Moderate authorization helps ensure your cloud systems are secure and meet stringent federal standards, in addition to meeting CMMC requirements. If a cloud service that stores, processes, or transmits CUI does not have a FedRAMP authorization, then the Cloud Service Provider must provide a body of evidence created by a certified FedRAMP third-party assessment organization (3PAO) that documents that the cloud service does satisfy all requirements of the FedRAMP moderate baseline. It is ultimately your responsibility to ensure the cloud services you use have a FedRAMP ATO or that they satisfy the DoD’s requirements to demonstrate equivalence.
When preparing your scope for assessment, in terms of compliance and scope impact, be sure you categorize your External Service Providers based on their roles and whether they interact with Controlled Unclassified Information (CUI) or Security Protection Data, or SPD.
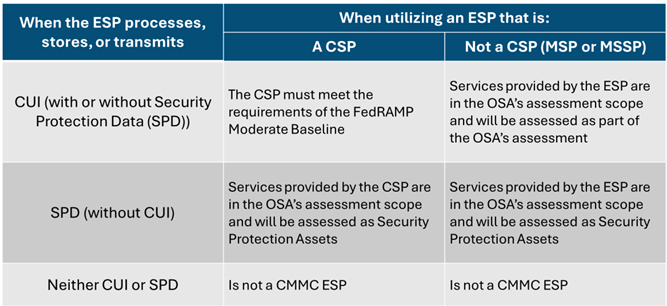
Additionally, the use of an ESP, the relationship to the OSC, and the services provided need to be documented in the contractors System Security Plan along with the services described in the ESP’s service description and customer responsibility matrix. Furthermore, if a contractor’s CUI or Security Protection Data (SPD) flows to the ESP, that ESP is in considered in scope of an assessment.
So, what is SPD? And how did the DoD come up with this definition?
Per the Final Rule, “SPD is configuration security relevant information and includes but is not limited to: Configuration data required to operate a Security Protection Asset (SPA), log files generated by or ingested by a SPA, data related to the configuration or vulnerability status of in scope assets, and passwords that grant access to the in-scope environment.”
The DoD considered the NIST definitions for System Information and Security Relevant information in the development of the CMMC definition for SPD and defines it as “data stored or processed by Security Protection Assets (SPA) that are used to protect an OSC’s assessed environment.”
The Value of the ESP: Your Ally in CMMC Assessment Success
While there is no “easy button” when it comes to tackling a CMMC compliance program, choosing the right external service provider can simplify the process and reduce the cost and risk of assessment failure. ESPs aren’t just service providers; they’re your strategic allies, playing a vital role in enhancing operational efficiency and meeting compliance for organizations in the defense base. By assuming full or partial responsibility for specific security and compliance objectives, ESPs significantly reduce the burden on contractors, enabling them to focus on core business operations. With a good ESP in place, your organization will inherit industry-leading best practices, capabilities, security measures, shortening the learning curve and lowering risk for your organization, creating a clear path to CMMC certification success.
This partnership model also allows contractors the ability to inherit robust controls and safeguards already being utilized by the ESP, strengthening their overall security posture without duplicating efforts.
Moreover, the right ESP will bring unparalleled expertise at economy of scale. They provide breadth and depth of specialized resources, often on a shared service basis, which makes accessing top-tier solutions more cost-effective and scalable. With a foundation of expertise and proven solutions, ESPs contribute value far beyond simple service provision; they empower organizations looking to achieve their security goals and scale with confidence.
ESPs, and Ensuring Assessment Success
In the Final Rule, the DoD states, “ESPs will be a driving force for our small to medium-sized businesses and their compliance with CMMC requirements. The ability of ESPs to create effective and economically feasible services will allow businesses to enclave different operations more easily and avoid unduly costly compliance expenses.”
Two Tracks, One Destination.
Are you on the right track? While the goal of achieving CMMC Level 2 compliance may be shared by many contractors, subcontractors and suppliers, everyone’s “path” of getting there will be unique. The way we see it, there are several tracks, with one secure and compliant destination.
Track 1: Going “All in”. This approach to CMMC compliance represents moving all systems, data and users into a secure, unified environment, such as Microsoft GCC High. This strategy offers a streamlined path by consolidating resources, standardizing security measures, and ensuring all Controlled Unclassified Information (CUI) and Federal Contract Information (FCI) are housed within a CMMC-compliant infrastructure. This eliminates the guesswork around which systems and assets are in-scope, creating a clear and enforceable security boundary for the enterprise.
Track 2: The Enclave Approach. The enclave approach creates a well-defined and focused security compliance boundary around only those systems and assets that handle CUI or FCI. By containing sensitive data and activities in this limited, isolated environment, your organization can maintain rigorous security standards without extending compliance efforts to the entire enterprise and network. Rather than moving all users and systems to a secure environment, which can represent a costly overhaul, the enclave approach allows for a more resource-efficient compliance strategy. This approach offers a practical balance of security, efficiency, and flexibility for meeting CMMC standards.
Final Thoughts and Next Steps
In scoping for CMMC, precision is paramount. Properly establishing your scope and leveraging the right External Service Provider to shepherd your organization through the process will save time, money and streamline your journey to CMMC Level 2 certification success.
Ready to get started?
Based on your organizations unique business and compliance goals, NeoSystems can help you choose a compliance track that’s right for you. For additional information on enclave options, download our white paper “Reduce the Scope and Cost of Protecting Federal Data with Enclaves”
Disclaimer. This guide provides general direction for CMMC Level 2 certification preparation. Consult official DoD documentation for specific compliance requirements.
References:
– 32 CFR Part 170
– CMMC Assessment Guide—Level 2’
-NIST 800-171a r2












